Vulnerable perimeter devices: a huge attack surface
5 (517) In stock

With the increase of critical gateway devices deployed to support off-premise work, companies across the world have to adapt to a new threat landscape where perimeter and remote access devices are now in the first line.

A Look at CISA's Top Routinely Exploited Vulnerabilities
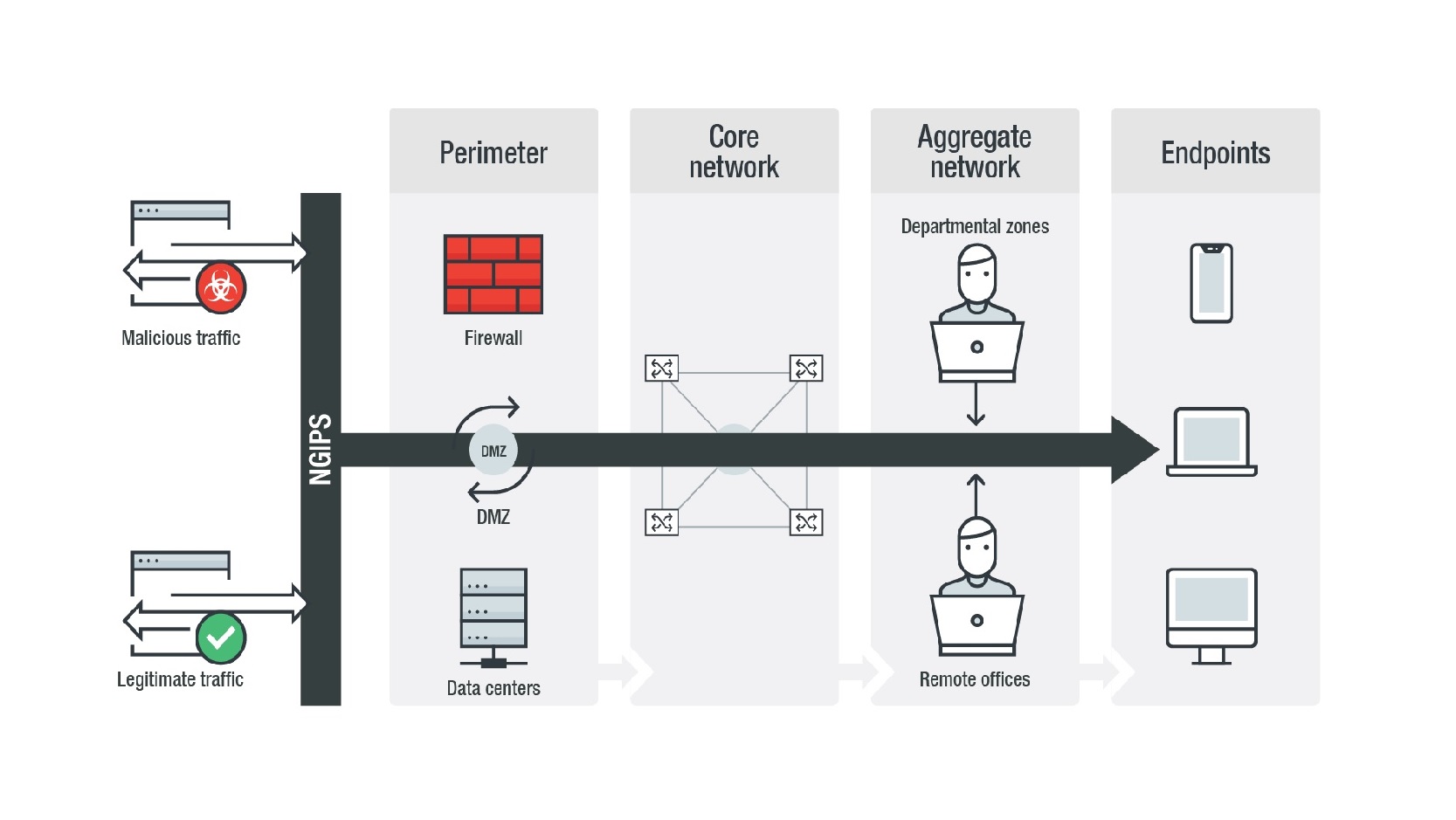
Guide to Network Threats: Strengthening Network Perimeter Defenses with Next-generation Intrusion Prevention - Security News
One-Click Attack Surface in Linux Desktop Environments

Cyber Signals Issue 3: The convergence of IT and OT and the risks

Viewing the profile for Ionut Ilascu
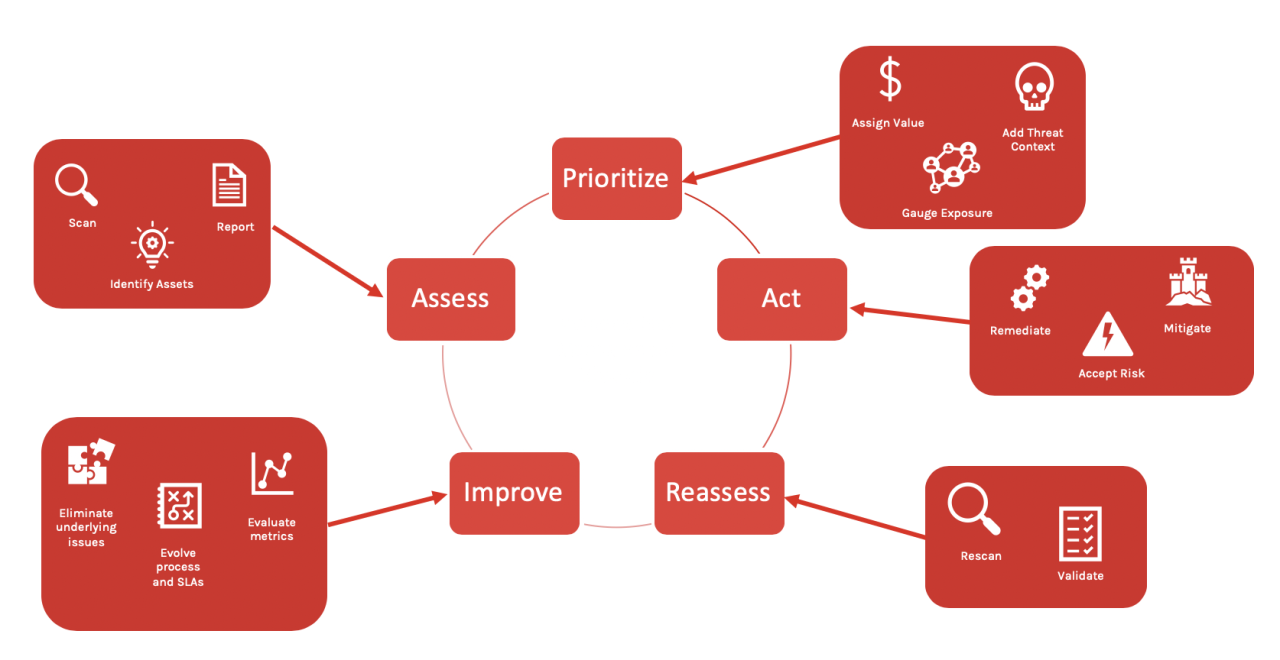
Maximizing the ROI of your Vulnerability Management Program with
Top 8 Attack Surface Management Solutions for 2022 - Spectral

5 Ways to Reduce Your Attack Surface, 2018-08-02
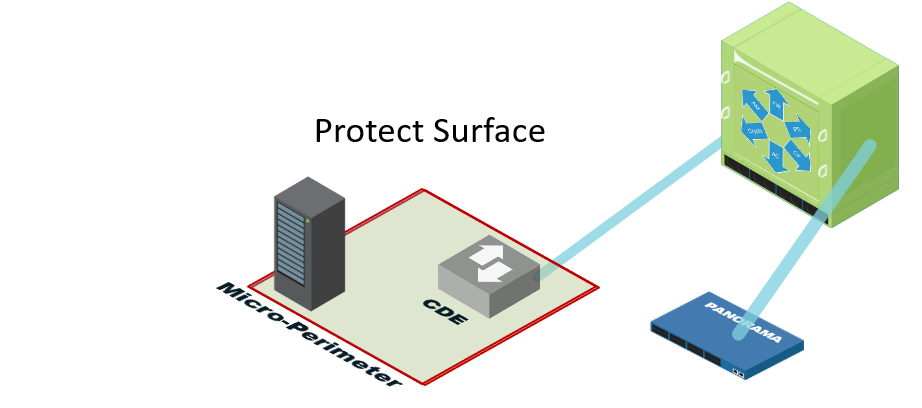
Define a Protect Surface to Massively Reduce Your Attack Surface
Perimeter Technologies Invisible Fence Replacement Collar 10K
Perimeter Device - an overview
Dog Fence Kits & Systems, Glenwood & Alexandria, MN
Perimeter 81 The World's First Cybersecurity Experience Platform
Teledyne FLIR, Magos forge technology partnership to elevate perimeter security
 Lion Brand Yarn - Basic Stitch Anti-Pilling - White 100g – CraftOnline
Lion Brand Yarn - Basic Stitch Anti-Pilling - White 100g – CraftOnline Step Up Your Fashion Game – 7 Shoe Styles to Wear with Midi Dresses - InStyle with Stacey
Step Up Your Fashion Game – 7 Shoe Styles to Wear with Midi Dresses - InStyle with Stacey Adored by Adore Me Women’s Morgan Natural Lift Lace Push Up Bra, Sizes 32B-40DD
Adored by Adore Me Women’s Morgan Natural Lift Lace Push Up Bra, Sizes 32B-40DD 2x CD - Paramore - Paramore - #A1828
2x CD - Paramore - Paramore - #A1828- Women's UA Rival Fleece Big Logo Hoodie
 Womens Plastic Garden Clog Ladies Waterproof Clog Summer Sandals Size 7 8 9 10 11 12 White
Womens Plastic Garden Clog Ladies Waterproof Clog Summer Sandals Size 7 8 9 10 11 12 White
