Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui
4.9 (334) In stock
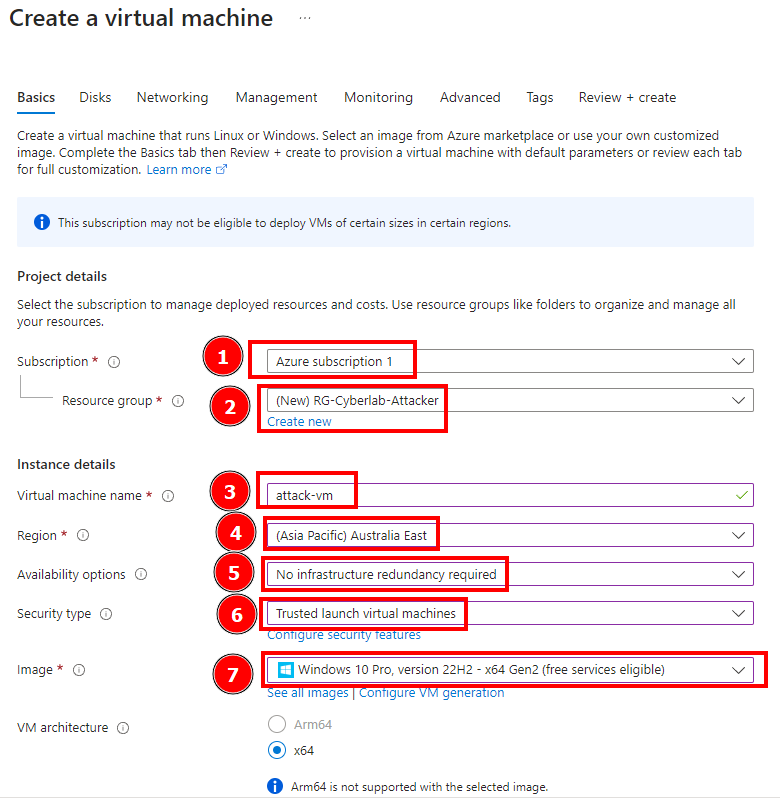
In this session we’re going to simulate an attack from another VM and then observe the attacker’s log. First we create an attacker VM. This VM’s name is attack-vm and also contain a different…
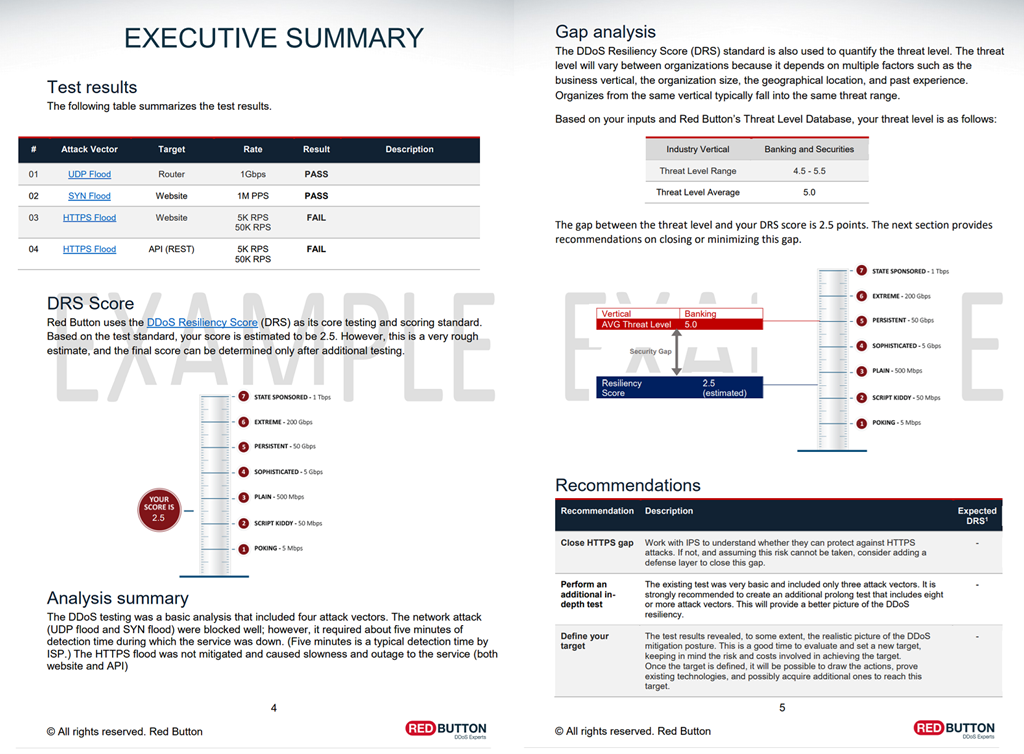
Tutorial: Azure DDoS Protection simulation testing
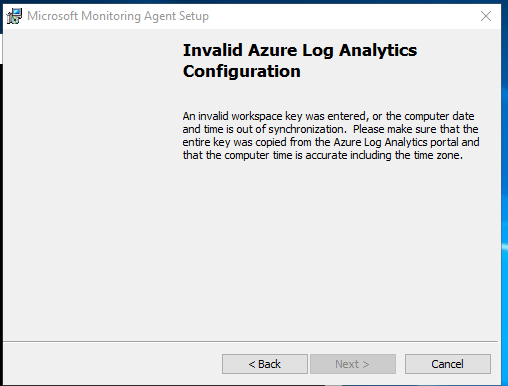
Issue With OMS Gateway - Microsoft Q&A

Detection, differentiation and localization of replay attack and false data injection attack based on random matrix
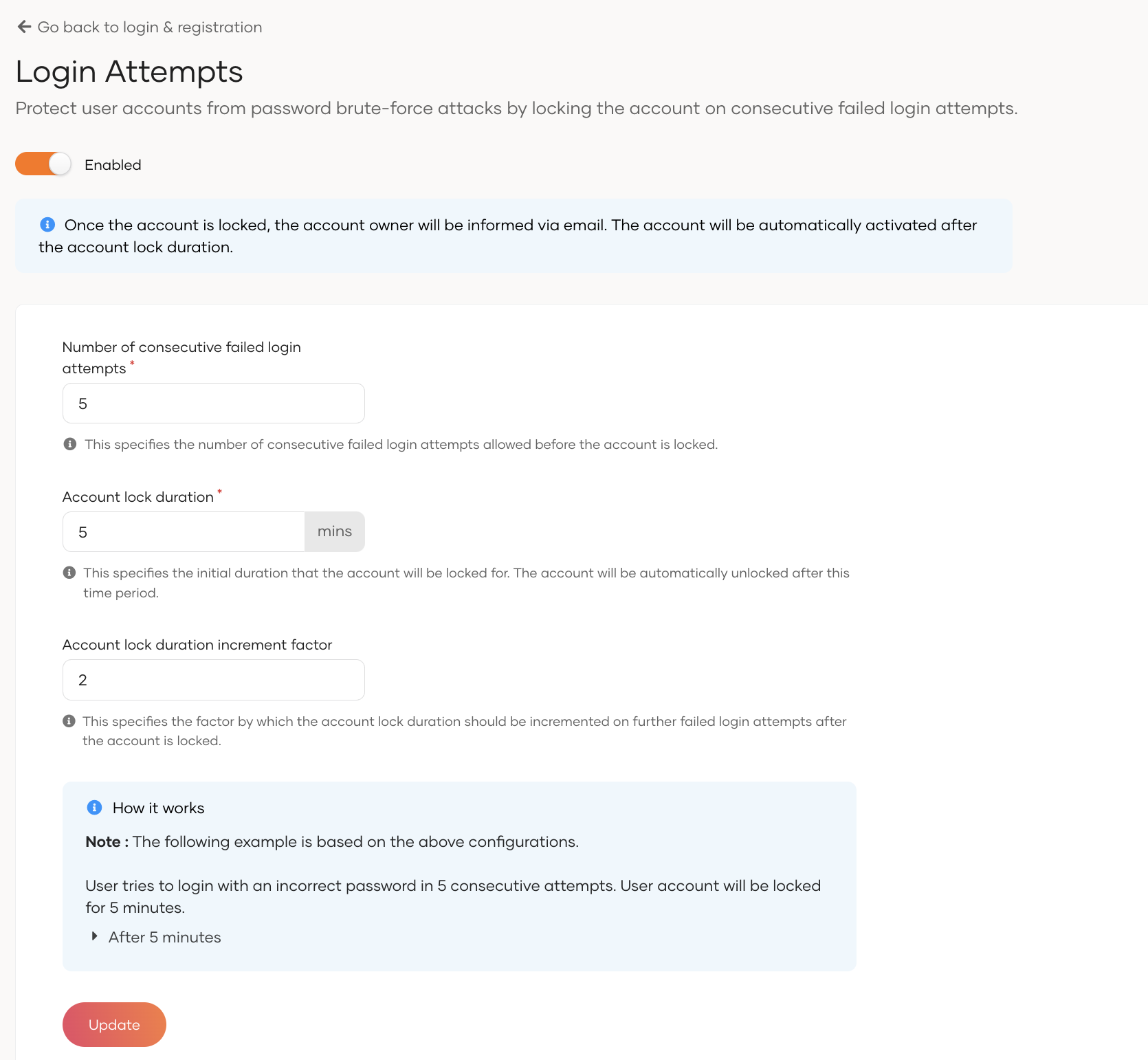
Configure login-attempts security
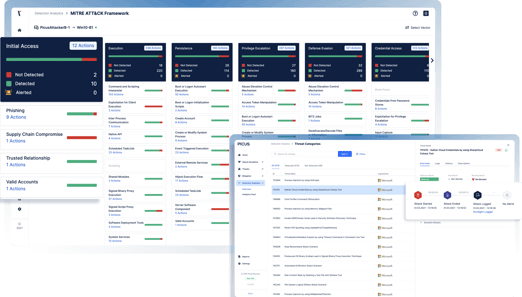
Log Validation with Attack Simulation

Simulating 2 drones with SITL/Airsim in Windows/Cygwin won't work - Copter Simulation - ArduPilot Discourse

Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui

Detection, differentiation and localization of replay attack and false data injection attack based on random matrix
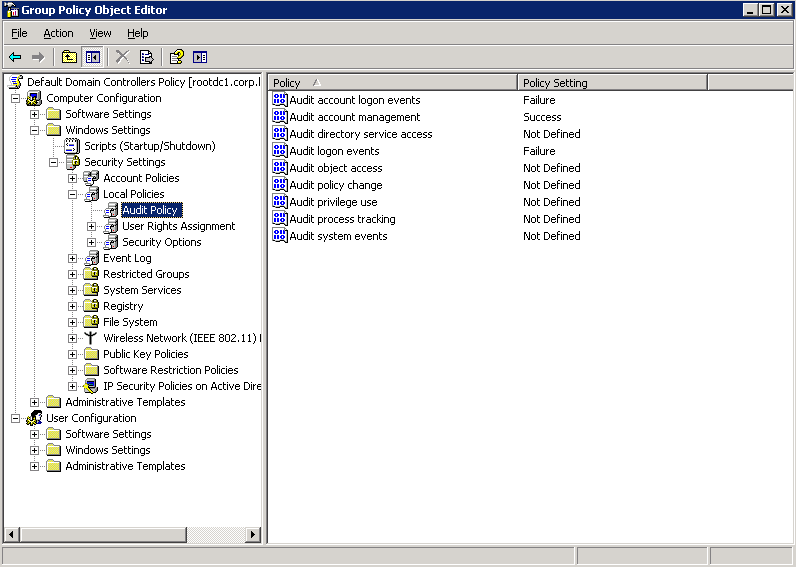
How to find failed login attempts in Active Directory
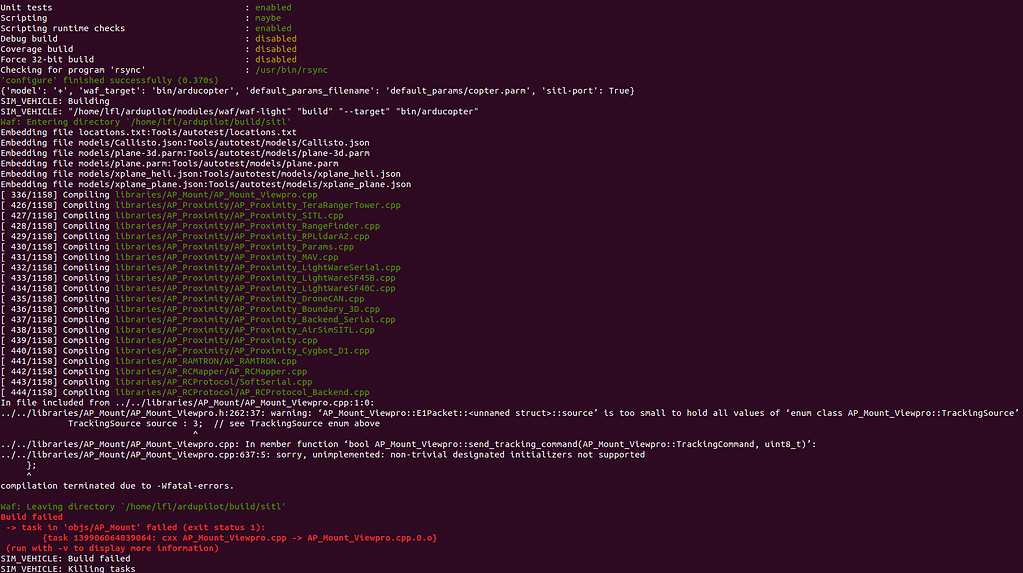
Sim_vehicle.py --map --console:task in 'objs/AP_Mount' failed - ArduCopter - ArduPilot Discourse

Part 9: Microsoft Sentinel Incident Response., by Duyet Bui
OWASP-Testing-Guide-v5/document/4_Web_Application_Security_Testing/4.11_Business_Logic_Testing/4.11.2_Test_Ability_to_Forge_Requests_OTG-BUSLOGIC-002.md at master · 0x4ghs/OWASP-Testing-Guide-v5 · GitHub

Microsoft Attack Simulation URLs - Anti-Virus Blad - Check Point CheckMates
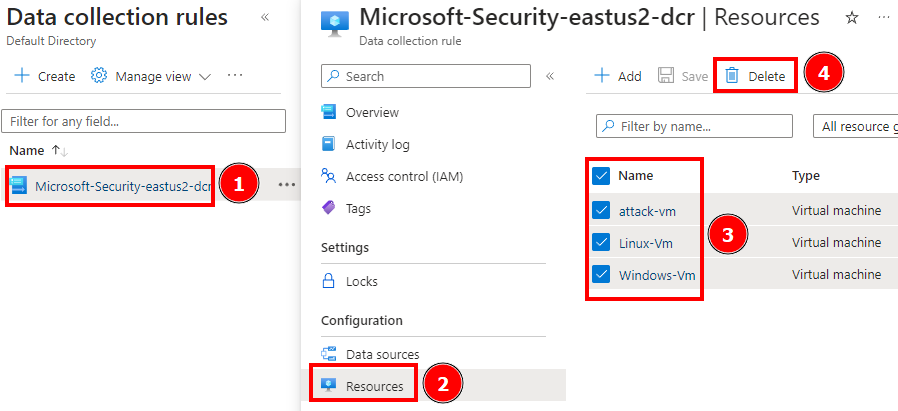
Part 5: Configuring/Collection Windows Security Event Logs and Syslog Logs and for Log Analytics Workspace., by Duyet Bui
Coats Co. Classy Wool Blend Coat by Anne Klein
DIY KIM KARDASHIAN SKIMS, $25 COMFORTER TO FUZZY 3 PIECE SET, THRIFTED TRANSFORMATION VIDEO - YouT…
Kim Cattrall and Nelly Furtado Are the New Faces (and Bodies) of Skims
Kraft Cheese, Shredded, Mozzarella, Low-Moisture Part-Skim 8 oz, Mozzarella & Provolone
Part 2 of 4. If I'm talking too long or too slow, you can either skip
 Pure Demi Cup T-Shirt Bra – Montelle Intimates
Pure Demi Cup T-Shirt Bra – Montelle Intimates- The North Face Training Flex Mid Rise Leggings In Lilac Dye Print-Purple for Women
 Ranking the 10 Best Shoes of the 2022-23 NBA Regular Season
Ranking the 10 Best Shoes of the 2022-23 NBA Regular Season 2023 - Pantalones de lino de algodón para mujer, cinturón de pajarita, pierna ancha, pantalones de yoga palazzo, pantalones de verano para la playa, pantalones casuales elegantes 01*Negro 2XL 01*Negro Xishao ropa
2023 - Pantalones de lino de algodón para mujer, cinturón de pajarita, pierna ancha, pantalones de yoga palazzo, pantalones de verano para la playa, pantalones casuales elegantes 01*Negro 2XL 01*Negro Xishao ropa Hanes Originals Men's Cotton Shorts, 7
Hanes Originals Men's Cotton Shorts, 7 Amante Ultimo Original Strapless Padded Wired Multiway Bra Sandalwood (34D) - E0006C007134C in Chennai at best price by Ankur - Justdial
Amante Ultimo Original Strapless Padded Wired Multiway Bra Sandalwood (34D) - E0006C007134C in Chennai at best price by Ankur - Justdial
:quality(80):fill(white)/https:%2F%2Fimages.asos-media.com%2Fproducts%2Fthe-north-face-training-flex-mid-rise-leggings-in-lilac-dye-print%2F203303921-1-lilac%3F$XXL$)