Computer Systems Security (Cs-426), PDF
4.8 (634) In stock

CSS Final2020 - Free download as PDF File (.pdf), Text File (.txt) or read online for free.

A Review: Network Security Based On Cryptography & Steganography Techniques
Cryptography An introduction to one of the backbones of the digital world Cryptography is one of the most important aspects of information technology

Cryptography: Algorithms, Protocols, and Standards for Computer Security

Supercomputer - Wikipedia

CS 426 : Computer Security - Purdue
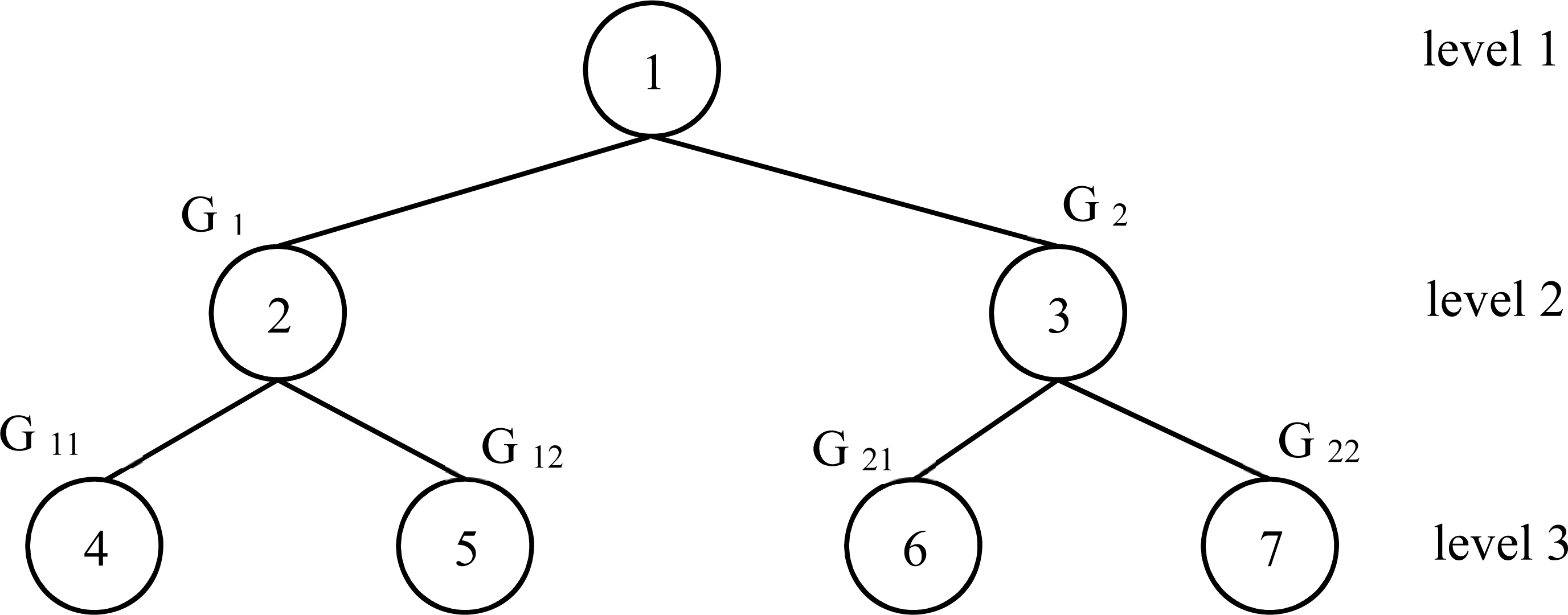
Architecture and enhanced-algorithms to manage servers-processes into network: a management system [PeerJ]
MS Program, Computer Science

CS 426 : Computer Security - Purdue
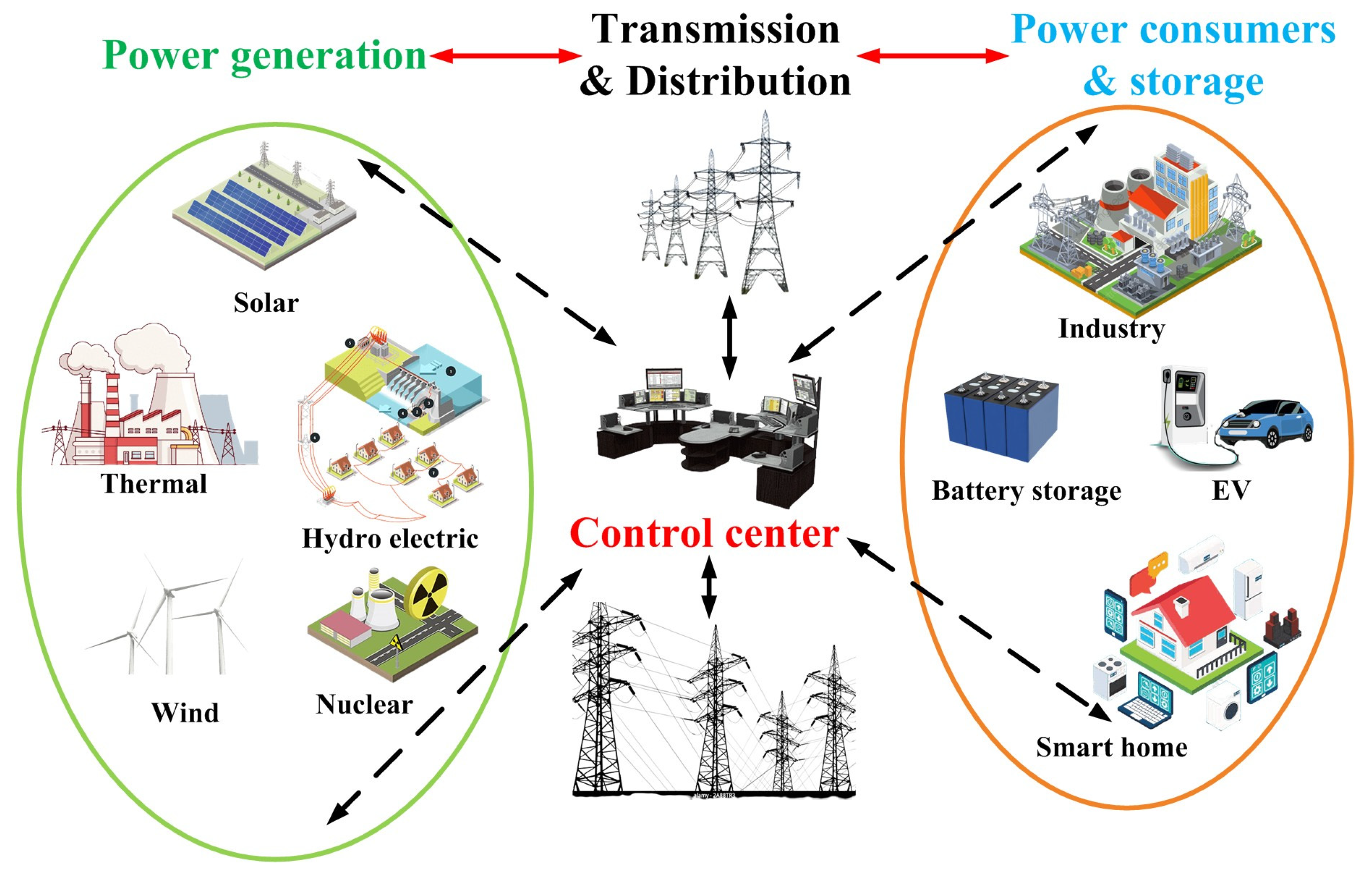
Energies, Free Full-Text

CS-426 Computer Security

Multiple Approach Paths to Insider Threat (MAP-IT): Intentional, Ambivalent and Unintentional Insider Threats

i1.rgstatic.net/publication/357393481_A_Systematic
CS-426 Hip Tie Satin Lace Sets – Orchard Corset
Cotton Hourglass Curve Longline Underbust Corset with Hip Ties : CS-426
Orchard Corset — CS-426 standard with hipties, CS-426 longline with
Corset Product Review: The CS-426 Standard Steel Boned Corset
PPT - CS 426 (Fall 2010) PowerPoint Presentation, free download - ID:1164550
 Kids BIG Cork Yoga & Non-Toxic Play Mat Cork Yoga Mat for Children– Scoria World
Kids BIG Cork Yoga & Non-Toxic Play Mat Cork Yoga Mat for Children– Scoria World Flexi answers - How do you convert 36 degrees Fahrenheit to Celsius?
Flexi answers - How do you convert 36 degrees Fahrenheit to Celsius?- Alexandra Bee Blog: The Diaper Heroes
 Just Rider Sports Leg Sleeves Calf - Medium - White Knee Support
Just Rider Sports Leg Sleeves Calf - Medium - White Knee Support Nappa leather trousers, black Pants for Women
Nappa leather trousers, black Pants for Women Wholesale Prom Dresses USA Formal & Bridesmaid Dresses
Wholesale Prom Dresses USA Formal & Bridesmaid Dresses
