CS426Network Security1 Computer Security CS 426 Network Security (1) - ppt download
5 (551) In stock

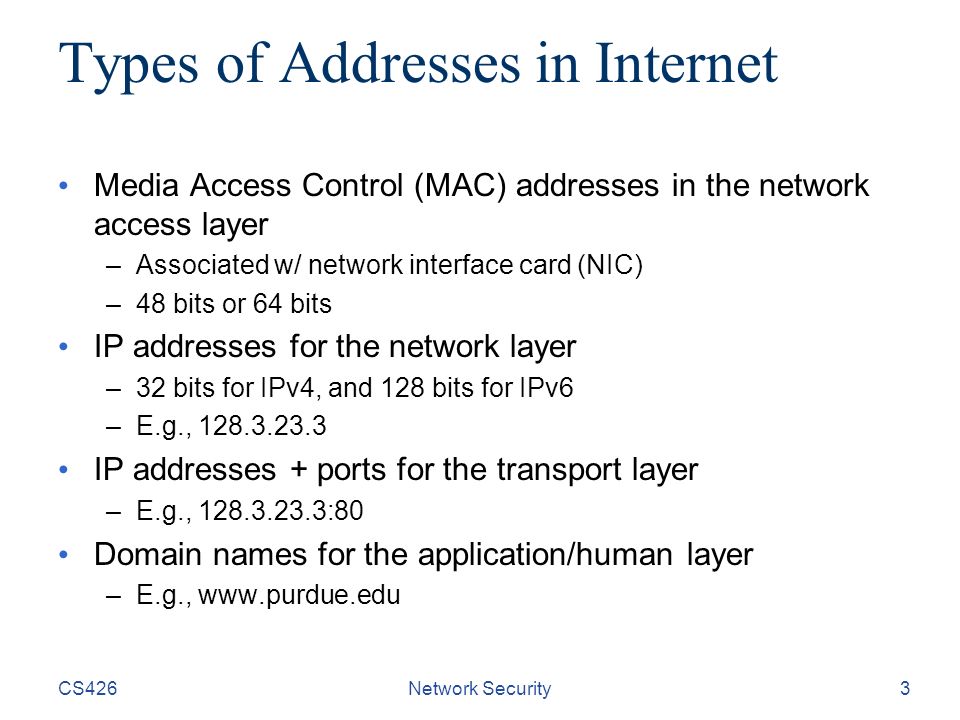
Types of Addresses in Internet Media Access Control (MAC) addresses in the network access layer –Associated w/ network interface card (NIC) –48 bits or 64 bits IP addresses for the network layer –32 bits for IPv4, and 128 bits for IPv6 –E.g., IP addresses + ports for the transport layer –E.g., :80 Domain names for the application/human layer –E.g., CS426Network Security3
CS426Network Security1 Computer Security CS 426 Network Security (1)
CS426Network Security2 Network Protocols Stack Application Transport Network Link Application protocol TCP protocol IP protocol Data Link IP Network Access IP protocol Data Link Application Transport Network Link
Routing and Translation of Addresses Translation between IP addresses and MAC addresses –Address Resolution Protocol (ARP) for IPv4 –Neighbor Discovery Protocol (NDP) for IPv6 Routing with IP addresses –TCP, UDP, IP for routing packets, connections –Border Gateway Protocol for routing table updates Translation between IP addresses and domain names –Domain Name System (DNS) CS426Network Security4
Threats in Networking Confidentiality –Packet sniffing Integrity –Session hijacking Availability –Denial of service attacks Common –Address translation poisoning attacks –Routing attacks CS426Network Security5
CS426Network Security6 Concrete Security Problems ARP is not authenticated –APR spoofing (or ARP poisoning) Network packets pass by untrusted hosts –Packet sniffing TCP state can be easy to guess –TCP spoofing attack Open access –Vulnerable to DoS attacks DNS is not authenticated –DNS poisoning attacks
CS426Network Security7 Address Resolution Protocol (ARP) Primarily used to translate IP addresses to Ethernet MAC addresses –The device drive for Ethernet NIC needs to do this to send a packet Also used for IP over other LAN technologies, e.g., FDDI, or IEEE Each host maintains a table of IP to MAC addresses Message types: –ARP request –ARP reply –ARP announcement
–To have other machines associate IP addresses with the attacker’s MAC Defenses –static ARP table –DHCP snooping (use access control to ensure that hosts only use the IP addresses assigned to them, and that only authorized DHCP servers are accessible). –detection: Arpwatch (sending when updates occur), Legitimate use –redirect a user to a registration page before allow usage of the network.
CS426Network Security10 IP Routing Internet routing uses numeric IP address Typical route uses several hops Meg Tom ISP Office gateway Source Destination Sequence Packet
AliceBob Eve Network Prevention: Encryption (IPSEC, TLS).
CS426Network Security12 User Datagram Protocol IP provides routing –IP address gets datagram to a specific machine UDP separates traffic by port (16-bit number) –Destination port number gets UDP datagram to particular application process, e.g., :53 –Source port number provides return address Minimal guarantees –No acknowledgment –No flow control –No message continuation
CS426Network Security13 Transmission Control Protocol Connection-oriented, preserves order –Sender Break data into packets Attach sequence numbers –Receiver Acknowledge receipt; lost packets are resent Reassemble packets in correct order BookMail each pageReassemble book
The sequence number of the actual first data byte is this sequence number plus 1. –If the SYN flag is clear, then this is the accumulated sequence number of the first data byte of this packet for the current session. Acknowledgment number (32 bits) – –If the ACK flag is set then this the next sequence number that the receiver is expecting. –This acknowledges receipt of all prior bytes (if any). CS426Network Security14.
CS426Network Security15 TCP Handshake C S SYN (seq=x) SYN ACK (ack=x+1 seq=y) ACK (ack=y+1,seq=x+1) Listening Store data Wait Connected
Adversary: do not have full control over the network, but can inject packets with fake source IP addresses –E.g., control a computer on the local network TCP sequence numbers are used for authenticating packets Initial seq# needs high degree of unpredictability –If attacker knows initial seq # and amount of traffic sent, can estimate likely current values –Some implementations are vulnerable.
CS426Network Security17 Blind TCP Session Hijacking A, B trusted connection –Send packets with predictable seq numbers E impersonates B to A –Opens connection to A to get initial seq number –DoS B’s queue –Sends packets to A that resemble B’s transmission –E cannot receive, but may execute commands on A Server A B E Attack can be blocked if E is outside firewall.
Inject data into an unencrypted client-to-server traffic, such as ftp file downloads, http responses. IP addresses often used for preliminary checks on firewalls or at the service level. Hide origin of malicious attacks. Carry out MITM attacks on weak cryptographic protocols. –often result in warnings to users that get ignored Denial of service attacks, such as resetting the connection..
number for an existing connection: –Attacker can send Reset packet to close connection. Results in DoS. –Naively, success prob. is 1/2 32 (32-bit seq. #’s). –Most systems allow for a large window of acceptable seq. #’s Much higher success probability. Attack is most effective against long lived connections, e.g. BGP..
CS426Network Security20 Denial of Service Attacks: SYN Flooding C S SYN C1 Listening Store data SYN C2 SYN C3 SYN C4 SYN C5
CS426Network Security21 SYN Flooding Attacker sends many connection requests –Spoofed source addresses Victim allocates resources for each request –Connection requests exist until timeout –Old implementations have a small and fixed bound on half-open connections Resources exhausted requests rejected No more effective than other channel capacity- based attack today
CS426Network Security22 Smurf DoS Attack Send ping request to broadcast addr (ICMP Echo Req) Lots of responses: –Every host on target network generates a ping reply (ICMP Echo Reply) to victim –Ping reply stream can overload victim Prevention: reject external packets to broadcast address gateway DoS Source DoS Target 1 ICMP Echo Req Src: Dos Target Dest: brdct addr 3 ICMP Echo Reply Dest: Dos Target
CS426Network Security23 Internet Control Message Protocol Provides feedback about network operation –Error reporting –Reachability testing –Congestion Control Example message types –Destination unreachable –Time-to-live exceeded –Parameter problem –Redirect to better gateway –Echo/echo reply - reachability test –Timestamp request/reply - measure transit delay
CS426Network Security24 Distributed DoS (DDoS)
CS426Network Security25 Hiding DDoS Attacks Reflection –Find big sites with lots of resources, send packets with spoofed source address, response to victim PING => PING response SYN => SYN-ACK Pulsing zombie floods –each zombie active briefly, then goes dormant; –zombies taking turns attacking –making tracing difficult
CS426Network Security26 Cryptographic network protection Solutions above the transport layer –Examples: SSL and SSH –Protect against session hijacking and injected data –Do not protect against denial-of-service attacks caused by spoofed packets Solutions at network layer –Use cryptographically random ISNs [RFC 1948] –More generally: IPsec –Can protect against session hijacking and injection of data denial-of-service attacks using session resets
CS426Network Security27 Readings for This Lecture Optional Reading Steve Bellovin: A Look Back at Security Problems in the TCP/IP Protocol Suite Steve Bellovin: A Look Back at Security Problems in the TCP/IP Protocol Suite
CS426Network Security28 Coming Attractions … DNS Security

CS 426 : Computer Security - Purdue
CS426Network Security1 Computer Security CS 426 Network Security

CS 426 : Computer Security - Purdue

CS426Network Security1 Computer Security CS 426 Network Security

CS426Network Security1 Computer Security CS 426 Network Security

CS426Network Security1 Computer Security CS 426 Network Security

Chapter 1 Presentation

CS426Network Security1 Computer Security CS 426 Network Security

Computer security

Network security ppt
CS-426 STANDARD length underbust (with hip ties), Orchard Corset
GitHub - serhataras/CS426-Parallel-Programming: Bilkent University
We always love how @sammitery styles her corsets! How do you wear
 CALÇA LEGGING MONTARIA TÉRMICA EM CORINO 014858 VERDE
CALÇA LEGGING MONTARIA TÉRMICA EM CORINO 014858 VERDE WOMEN'S FRONT HOOK & EYE CLOSURE SPORTS BRA SIZE 42 (EU 95) PINK
WOMEN'S FRONT HOOK & EYE CLOSURE SPORTS BRA SIZE 42 (EU 95) PINK Sweatshirt adidas Tiro 21 Training Top
Sweatshirt adidas Tiro 21 Training Top- Giannis stopper' Semi Ojeleye has found a fit with Milwaukee Bucks
 Curious George Women's Top and Bottom Set, Bra
Curious George Women's Top and Bottom Set, Bra Bernat® Blanket™ #6 Super Bulky Polyester Yarn, Weathered Wood 10.5oz/300g, 220 Yards (4 Pack)
Bernat® Blanket™ #6 Super Bulky Polyester Yarn, Weathered Wood 10.5oz/300g, 220 Yards (4 Pack)